Greetings...😇!
Thank You, guys...Keep cooperating...
💥I think we are familiar now, so without any formalities let's come to the point. As mentioned in my last post (link - https://securityencoder.blogspot.com/2020/07/hacking-terminologies.html ), let's start with some important tools and OS(Operating System) related to hacking.
"Important tools for hacking"
A hacking tool is a software or a framework used for hackingpurposes. Some of the famous hacking tools are the Metasploit framework, Nmap, Aircrack-ng, Wireshark, Hydra, and many others are there.
👉Let's discuss some major tools involved in hackingpractices:
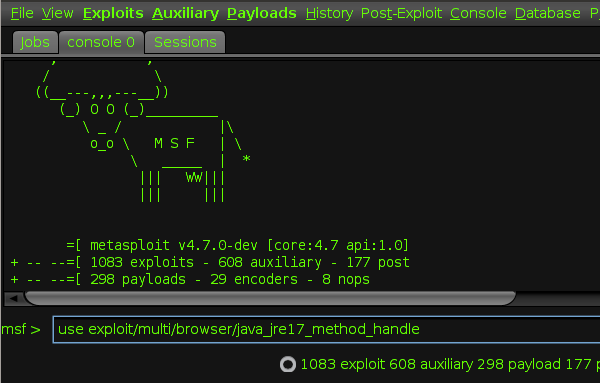
1. Metasploit Framework:
This tool is mainly used by most of the white hat hackers. Metasploit Framework comes with downloadable modules allowing the hacker exploiting, executing payload, cracking the vulnerabilities.
2. Nmap:
Nmap is one of the most useful tools for network security scanning. Nmap can be used to identify hosts, scanning open ports, and show you what devices are open for your network.
3. Wireshark:
Wireshark is a well-known tool that discovers vulnerabilitieswithin a network and probes firewall rule-sets. It is used by lots of security professionals. Wireshark allows you to read data from various systems.
4. Aircrack-ng:
Aircrack-ng is a very good tool to assess Wi-Fi network security. Major uses are checking Wi-Fi cards and capabilities, attacking fake access points, packet injection, data capturing, and processing further, cracking.
5. Hydra:Hydra Framework is a new, principled approach to modeling and detecting security-critical bugs. Hydraprovides a rigorous and cost-effective brute online password cracking program.
⏩ After being familiar with the tools, let's move to the main hacking environment we will use to launch practical hacking attacks. We use operating systems like Kali Linux (Parrot and many more are also there) for further processes.
💥Kali Linux :
👉Kali Linux is a provider of world-class information security training and penetration testing services. Kali Linux comes with several network services that may be used in various situations and is disabled by default from the time of installation. Kali Linux is provided by Offensive Securityalong with free certified ethical hacking courses, Metasploit Unleashed.
⏩ Installing Kali Linux on the virtual box:
Hey guys, the actual installation process involves many steps, screenshots, and directions which are very difficult to display here and that should be done under professional and expert guidance. I am sorry that I am not able to elaborate on the overall process of installation but I am providing sources that will help you to do it.
1. First of all download Oracle Virtualbox from the link https://www.virtualbox.org/wiki/Downloadsclick on "windows host" and you will get it.
2. Download the official .iso or .viso image file of Kali Linux from their official website. Here is the direct link to the page https://www.offensive-security.com/kali-linux-vm-vmware-virtualbox-image-download/#1572305786534-030ce714-cc3b

3. After this you can go to the Youtube videos to install Kali Linux on your virtual machine many videos are available on Youtube. Refer this video , changes in versions can be possible.
💨After you install Kali Linux you will be able to configure your network and other settings. I recommend to get in touch with hacking handbooks and ethical hacking courses available on various online teaching platforms such as Udemy, Coursera, Edx, etc then and then only you should be able to understand hacking otherwise you will not understand what you are doing.
💣Are you thinking hacking is not possible on your android phone...you are WRONG..!
You can do various hacking practices on your android phoneitself!!!....isn't it exciting...means cracking a phone's security and exploiting into it, taking screenshots of the target phone, sending fake emails and messages to the victim, obtaining target IP and information by sending the link to the target, seeing apps available on someone's device, spying someone sitting right from your phone...!!
I think it's enough for this topic next post will be an 👀EXCITEMENT😃 for all the readers it will cover information about the lifestyle and attitude required to become a hacker and how to protect yourself from hacking attacks.
SEE YOU SOON...
Make a termux tutorial
ReplyDeleteDefinitely, a post soon...thanks for demand bro....let me cover metasploit and theory sessions in the next post and I will post termux tutorial I have worked on...keep on reading for that....
DeleteAwesome bro
ReplyDeleteThank you so much...If you really like blogs please do share the link with your friends and keep supporting and commenting...always looking for suggestions...we have a lot more posts to come...
Delete