"Denialof Service"
Hey Friends...😃
In the last series of posts, we have discussed hacking attacks, their types, wireless attacks(link here👀) their introduction, how they work and preventive measures let us discuss some famous attacks to hack a website i.e. DoS Attacks.
Let's see what is it?

👉Introduction:
DoS is the acronym for Denial of Service. DoS is an attack used to forbid the entry of the intended user to connect to a network or a website by disrupting the services of the host temporarily or indefinitely.
DoS attack is achieved by flooding the target machine or resource as a web server with too many requests simultaneously which results in system overload and server failure to respond to some other or legitimate users.
The effect of this can either be crashing the servers or slowing them down due to flooding and eventually stop.
The internet powers a lot of businesses and e-Commerce. So, cutting some business leads to the loss of the entire business.
👉Types of DoS Attacks:
There are many techniques that we are going to discuss but there are mainly two types of web attacks,
‣ DoS: This type of attack is as carried by a single host.
‣ DDoS:Stands for Distributed Denial of Service. This type of attack is performed by multiple numbers of machines or attackers that attack a common victim. It floods the network with data packets.

👉How it works:
Based on the working scenario, there are many techniques used under the name of the DoS attack. We will look at some of them and their working below:
1.Ping of Death Attack:
As the name suggests, a ping command is used to test the availability of network resources. It includes sending the data packets of relatively larger size(65,536 bytes) which cause the target machine to freeze or crash. This type of attack is less common today. Common is the ICMP(Internet Control Message Protocol) Flood Attack.
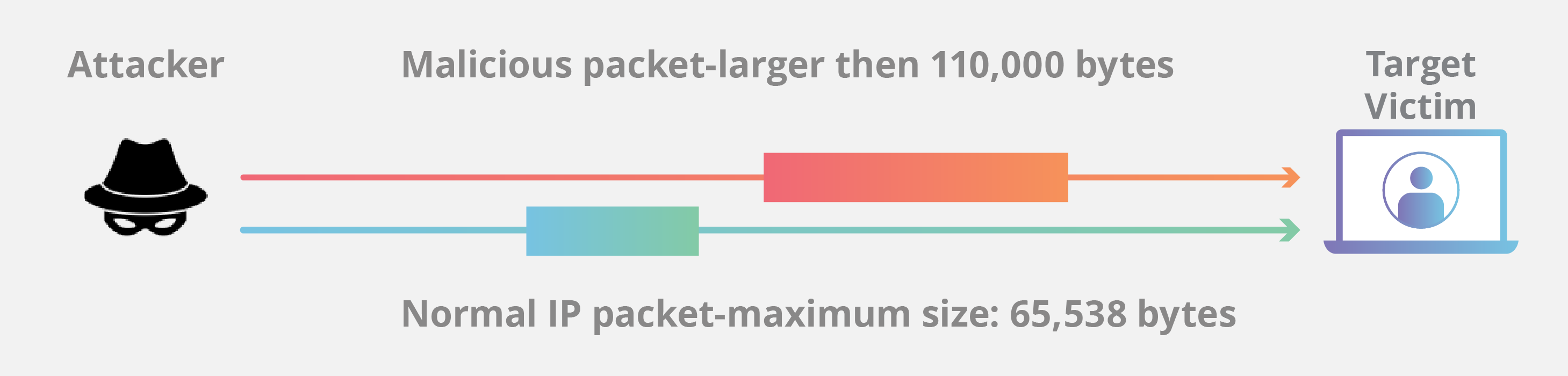
2.Smurf or ICMP Flood Attack:
TCP/IPsystems were never designed to handle packets larger than the maximum they crack into fragments, making them vulnerable to packets above that size. The reply IP address is spoofed to intended user. All the replies are sent to the victim instead of the IP. Since a single Internet Broadcast can support 255 hosts, smurf attack amplifies each ping 255 times causing slowing down of the server.
(We will be discussing TCP/IP concepts in the posts related to "Networking")
3.Buffer Overflow:
A buffer directs to temporary storage media in RAM that is used to hold data before CPU manipulates it before hard disk. This attack loads buffer with more data than it can hold causing the buffer to corrupt the data it holds.
4.Teardrop:
This type of attack uses larger data packets. Sending fragmented data packets to victim and are reassembled on the receiving host. During this packets manipulation by attacker causes overlap of these packets crashing the target device resulting in DoS. It works better on old operating systems due to bug in TCP/IP.
5.SYN Attack:
SYN is a short form for synchronization. It works by flooding victims with incomplete SYN messages. This causes the target machine to allocate memory resources that are never used and deny access to legitimate users.
👉Tools used for DoS Attack:
• Slowloris: It is a slow DoS script. It can build malicious sockets. It sends HTTP GET requests to the server but the request is not complete. Web server will wait for the request to complete and the resources are allocated. Parallel to these multiple threads of this kind is opened and thus the resources of the web server are exhausted. Refer to the diagram below. (Source: Internet)

• Botnets: These are a number of internet-connected devices, each of which is running one or more bots. The owner can control the botnet using command and control (C&C) software.
• Blast: BLAST Professional DOS brings easy-to-use, high-performance, error-free session serial communications to the DOS PC world. BLAST Professional DOS features the BLAST error-free session protocol, a suite of terminal emulators, and an extensive scripting language.
👉Prevention of DoS Attack:
• Indications of DoS attacks are slow network performance for files and websites, inability to load a particular website, sudden loss of connectivity across devices on the same network.
• Installing security patches can help reduce the chance of DoS attack.
• Firewalls can be used to block all traffic coming from an attacker by identifying his IP.
• Routers can be configured via the Access Control List to limit access to the network and drop suspected illegal traffic.
That's all for today...SEE YOU...Bye...😊😊
Comments
Post a Comment